
Application Security
Identify, eliminate and protect all kinds of applications such as Web, Mobile, Desktop, etc..

Network Security
Monitor and configure your network and data from breaches, intrusions and other threats

Cloud Security
Security measures to safeguard your cloud base data, applications, and infrastructure from cyber attacks.

IoT Security
Implement best practices to keep your IoT systems safe and secure from threats and breaches.

Source Code Review
A comprehensive examination of application source code to identify security related flaws and make it more robust.

Incident Response
An organized approach to address, manage and reduce Cyber attack or Security breach.

Security Operation Center
A managed SOC to continuously monitor and improve Security posture while preventing, analyzing and responding to Cyber Security incidents.

Digital Forensic
Investigate, uncover and interpret Cyber Crime or Fraud.
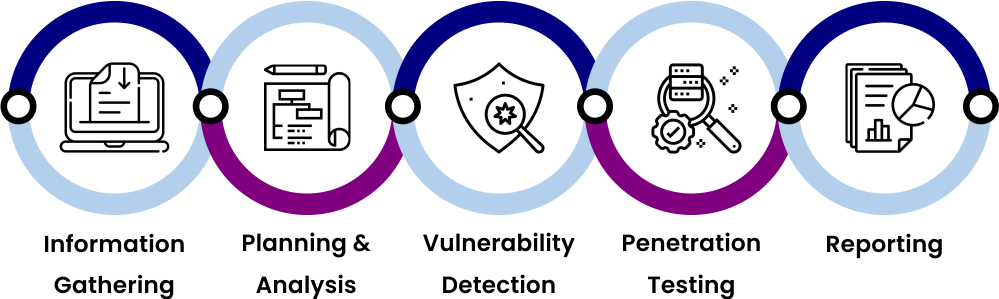
OUR APPROACH
How It Works?
WHY US?
Your trusted Partner
We understand and simplify Cyber Security for you by offering innovative and cutting edge solutions to become your trusted and reliable partner for every security challenge around and beyond




